PrivacyOps
The multi-disciplinary practice to automate compliance with privacy regulations.
Be responsible custodians of people's data - Take the FREE PrivacyOps course and get the eBook today.
What people are saying about
PrivacyOps Certification
PrivacyOps Course Outline
Filter Lessons By
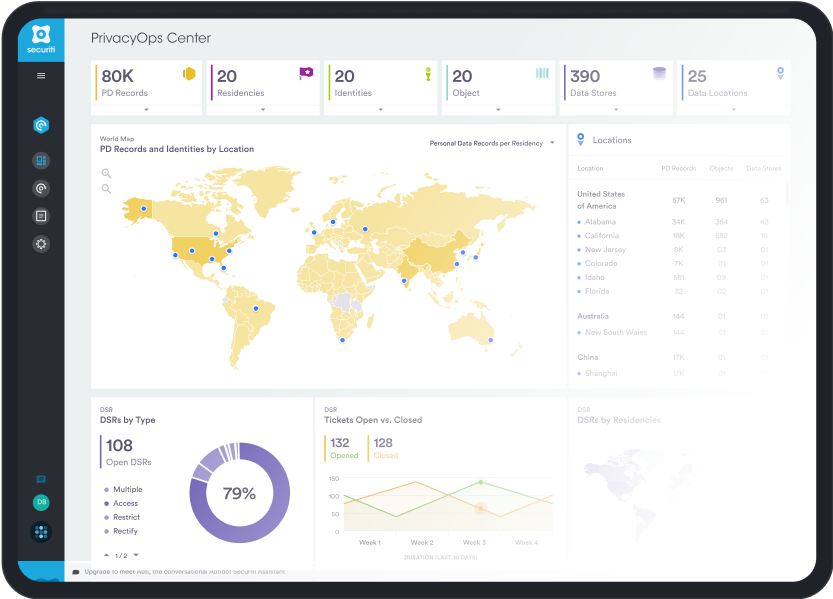
Easily Deploy a Fully Functional Privacy Center
Deploy a fully functional privacy center with an elegant frontend, fully automated backend and integrated privacy regulation intelligence.
Get the PrivacyOps eBook
PrivacyOps - Automation
& Orchestration for
Privacy Compliance
Download the eBook

At Securiti, our mission is to enable enterprises to safely harness the incredible power of data and the cloud by controlling the complex security, privacy and compliance risks.
Copyright © 2023 Securiti · Sitemap · XML Sitemap
Company
Resources
Terms
Get in touch
info@securiti.ai
3031 Tisch Way Suite 110 Plaza West, San Jose,
CA 95128